Simple SSH Tunnel Guide
Contents
About This Guide
This guide shows you how to set up a quick and dirty SSH tunnel from your workstation to a server in a remote, hard-to-get-at network. It makes use of a gateway machine in AWS to maintain the tunnel connection and includes all the tricks required to get through proxies and firewalls.
Please Note: This post is purely for interest's sake. I highly recommend you do not do this at your organisation as you may quickly find yourself on the wrong end of a workplace agreement violation.
The Server Bits
Three separate machines are involved in setting up the tunnel in this guide:
- 1 local machine to SSH from
- 1 remote machine to SSH into
- 1 AWS EC2 instance to act as a gateway
This guide assumes that your remote machine and gateway are running Ubuntu and your workstation is running OS X, however the configuration would not vary too much on other systems, and this guide could be adapted to support SSH client/server software running platforms including Red Hat and even Windows.
The Tunneling Example
The Goal: Establish a simple tunnel from a local workstation to a remote HTTP server.
The SSH tunnel in this example is made up of two persistent SSH connections - one from the local workstation side and one from the remote machine side. When established, the connections between the machines involved look like this:
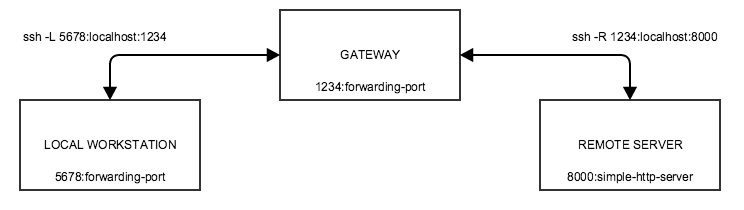 |
Here we have port 5678 opened up on the local workstation via an ssh -L connection which forwards connections to port 1234 on the gateway. From the remote side, the ssh -R connection forwards connections on port 1234 on to the remote servier on port 8000:
 |
The command above acts in the same way as if the following was executed on the remote server:
 |
This guide will take you through all the steps necessary to recreate this example.
Next Step
Please continue on to Part 1 - Building the Gateway for the next part of this guide.